Authentication and Authorization in the Oracle/Apex Environment
Companies working with Oracle and APEX know the challenge all too well – the standard mechanisms often fall short when it comes to meeting real-world authorization requirements.
dragon.XPF lets you tackle this topic with confidence – and it’s completely license-free.
Built on a well-structured authorization model (groups, roles, permission objects), dragon.XPF offers the flexibility to implement virtually any requirement.
Authentication
In times when the operational security of systems is even more important and single sign-on solutions are only used to a limited extent, we have decided on a standard that also meets user acceptance.
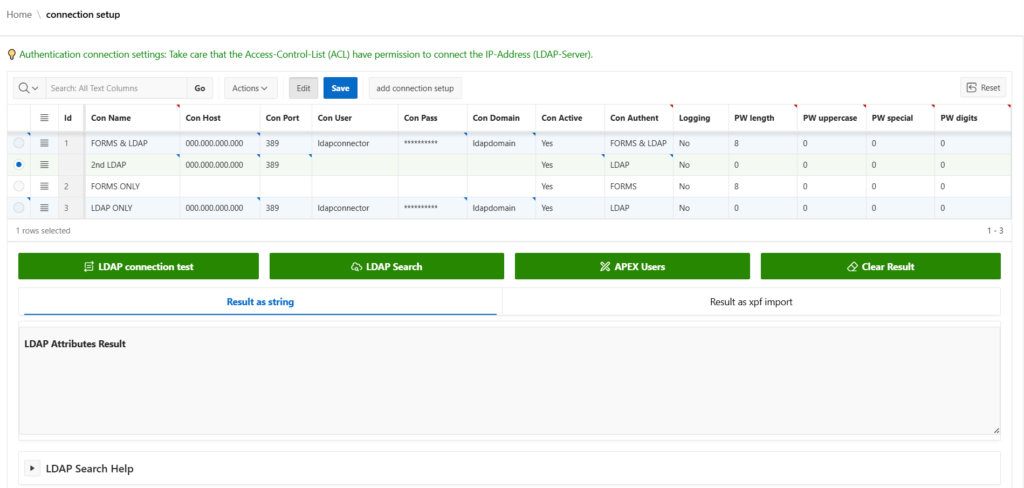
Through By connecting an LDAP connector, all users can authenticate themselves to all internal applications with their Windows domain password. Of course, it is also possible to operate the registration completely independently by using your own user management.
For example, it is possible to have the user base created via LDAP, but the authentication method FORMS within to keep the dragon.XPF.
- Easy connection to existing Oracle/Apex applications
- LDAP implementation based on the Active Directory standard
- Two-track authentication possible (LDAP and FORMS)
- User import possible via LDAP
- LDAP test center for checking queries (searchBase, scope, filter)
- Multi-factor authentication (MFA) can be set per Apex application and user
Authorization and User Management
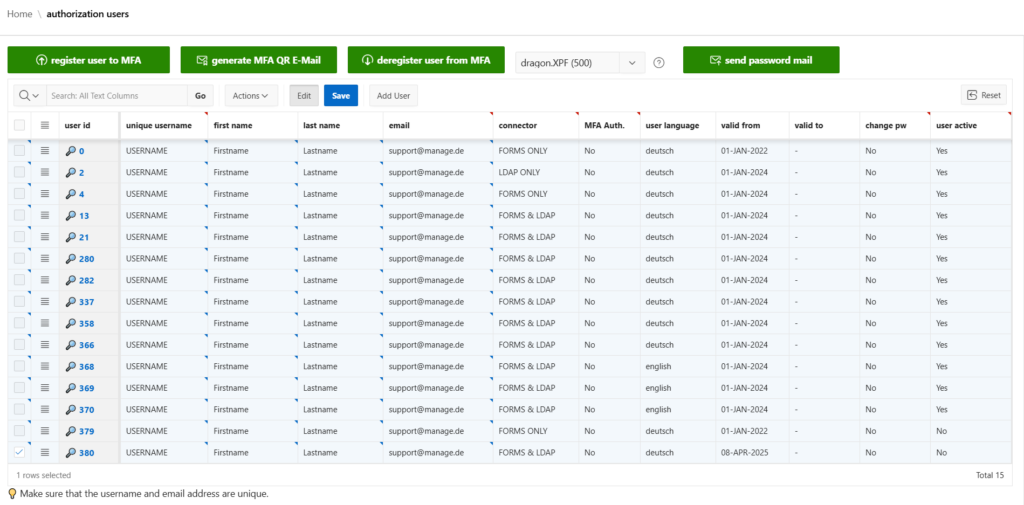
The greatest strength of the dragon.XPF tool is the ability to map any type of complex user authorization.
Knowing how quickly the requirements for the applications can increase within an application with many employees It is important to us to provide a highly scalable and well-designed solution.
- Freely configurable group and role concept
- Authorization objects based on the Apex Standard
- Easy connection to existing applications
- Consistent operating concept
User Details
Viewing a user’s profile reveals the flexibility of dragon.XPF. Permissions can be assigned at the level of groups, roles, or individual objects – all of which can be reviewed in the dedicated “Effective Privileges” section.
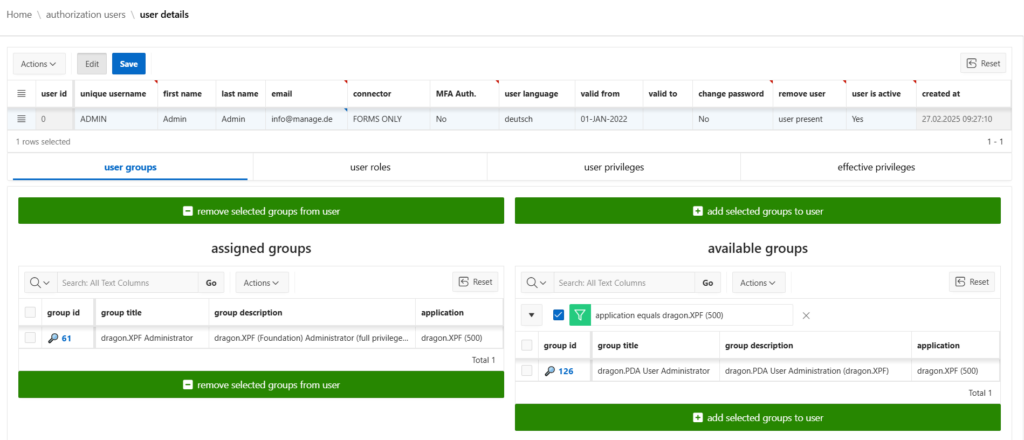
Details about the authorization objects
Based on the Oracle Apex Standard, it is possible to “compare” the authorization objects of your applications at any time. If new elements or entire pages are created, a so-called “privilege set” only needs to be created. This methodology carries out a fully automatic search of the application objects and compares them, i.e. objects that no longer exist are of course also removed.
Now the new authorization object only needs to be assigned to an existing or new role. If roles are part of groups, no further work (e.g. group generation) needs to be carried out and the employee can get started straight away.
For example, it is also possible to additionally edit an interactive grid using the read-only attribute to control. In addition, you can not only assign groups and roles to a user – you can also explicitly assign only a specific individual objectif necessary.
Strictly speaking, any authorization object can be generated that has the option of selecting an authorization controller in the “Security” area.
Overview of possible permission objects
- Application
- Page
- Breadcrumb Entry
- Application Computation
- Interactive Grid
- Interactive Grid Column
- Application Process
- List Entry
- Page Branch
- Page Button
- Page Computation
- Page Dynamic Action
- Page Chart Series
- Page Interactive Report Column
- Page Item
- Page Process
- Page Region
- Page Report Column
- Page Validation
Groups and Roles
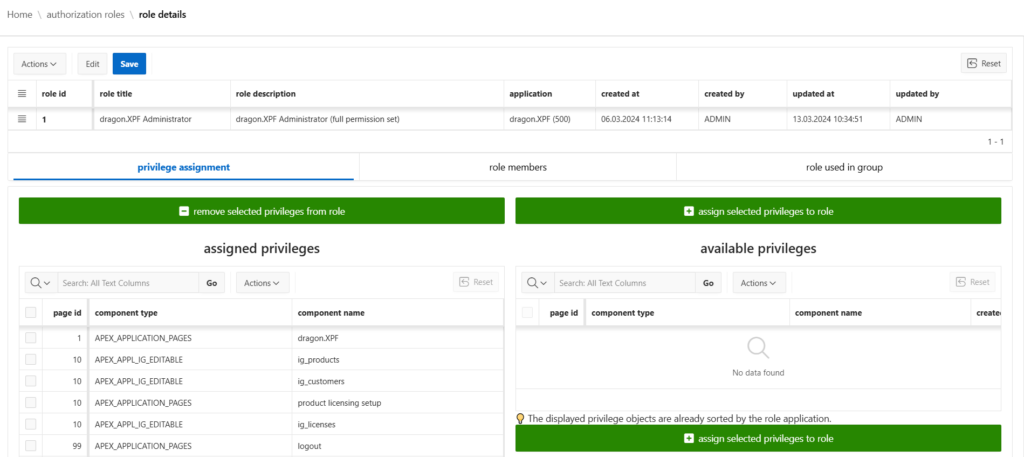
The creation of roles from permission objects and the creation of groups from roles follow the same logic – including identical conditions.
Thanks to these features, you always maintain a clear, transparent, and efficient overview of your entire permission structure.
Just don’t lose track…
Anyone who has worked with permissions in complex software systems knows how quickly things can get confusing when dealing with groups, roles, and permission objects. An overview of the most important features:
- display all users assigned to a specific role or group
- check in which roles or groups a permission object is used
- add or remove users directly within the same view
- see which groups a specific role is assigned to
- review which permission objects a user actually has
Technical Presentation (YouTube Video)
Do you have any questions?
Do not hesitate to contact us.